Difference between revisions of "W4503 Capture the Flag III"
(added prime multiplication writeup) |
(added no signal forensics writeup) |
||
| Line 42: | Line 42: | ||
Notice that the image size is 2741x1901. These are both prime numbers, so let's multiply them as the challenge instructs us. 2741 times 1901 is 5,210,641. When we format this in flag format, we get '''ahsCTF{5210641}'''. | Notice that the image size is 2741x1901. These are both prime numbers, so let's multiply them as the challenge instructs us. 2741 times 1901 is 5,210,641. When we format this in flag format, we get '''ahsCTF{5210641}'''. | ||
=== No Signal === | |||
<pre> | |||
[75 Points] | |||
</pre> | |||
The challenge also provides the files static1.png and static2.png. | |||
[[File:CTF3-Static1.png|thumb|center|static1.png]] | |||
[[File:CTF3-Static2.png|thumb|center|static2.png]] | |||
When we view the 2 provided image files, they seem to look like TV static. There are black and white pixels that seem to be randomly placed. However, there seems to be some text down the center, but it is difficult to decipher. Since we have two images, we can assume that we will have to use them together to reveal the message. In this case, we will have to XOR the corresponding pixels of each image. That means if we lay each image on top of each other, in each coordinate that there is one black and one white pixel the output will be a black pixel, and each coordinate where there is the same color pixel on the top and bottom will result in a white pixel (assuming white=0 and black=1). We can make a script to XOR each pixel, or we can simply use an image manipulation program to accomplish a similar idea, in this case, we used paint.net. We can put each image on a layer and then delete all white pixels on the top layer to emulate an XOR. We get this result: | |||
[[File:CTF3-StaticAnswer.jpg|thumb|center|staticAnswer.jpg]] | |||
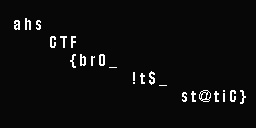
Therefore, the flag is '''ahsCTF{br0_!t$_st@tiC}'''. | |||
Revision as of 13:19, 19 January 2021
| Coming Soon | |
| This page will serve as the writeup for the CTF III competition problems that were released on January 12, 2021 |
Forensics[edit]
Prime Multiplication[edit]
[50 Points] There are 2 prime numbers associated with this image, multiply them together to get the flag.
Hint: flag format is ahsCTF{12345678}
The challenge also provides the file prime_multiplication.jpg.
We can examine the details of this image by using exiftool. Begin by downloading the image into the shell server using wget or SFTP. Then we can use exiftool to examine the metadata:
john-williams@codermerlin:~$ exiftool prime_multiplication.jpg
We get this output:
ExifTool Version Number : 11.88 File Name : prime_multiplicaton.jpg Directory : . File Size : 936 kB File Modification Date/Time : 2021:01:19 08:01:27-06:00 File Access Date/Time : 2021:01:19 08:01:26-06:00 File Inode Change Date/Time : 2021:01:19 08:01:27-06:00 File Permissions : rw-r--r-- File Type : JPEG File Type Extension : jpg MIME Type : image/jpeg JFIF Version : 1.01 Resolution Unit : inches X Resolution : 300 Y Resolution : 300 Exif Byte Order : Big-endian (Motorola, MM) Orientation : Horizontal (normal) Image Width : 2741 Image Height : 1901 Encoding Process : Baseline DCT, Huffman coding Bits Per Sample : 8 Color Components : 3 Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2) Image Size : 2741x1901 Megapixels : 5.2
Notice that the image size is 2741x1901. These are both prime numbers, so let's multiply them as the challenge instructs us. 2741 times 1901 is 5,210,641. When we format this in flag format, we get ahsCTF{5210641}.
No Signal[edit]
[75 Points]
The challenge also provides the files static1.png and static2.png.
When we view the 2 provided image files, they seem to look like TV static. There are black and white pixels that seem to be randomly placed. However, there seems to be some text down the center, but it is difficult to decipher. Since we have two images, we can assume that we will have to use them together to reveal the message. In this case, we will have to XOR the corresponding pixels of each image. That means if we lay each image on top of each other, in each coordinate that there is one black and one white pixel the output will be a black pixel, and each coordinate where there is the same color pixel on the top and bottom will result in a white pixel (assuming white=0 and black=1). We can make a script to XOR each pixel, or we can simply use an image manipulation program to accomplish a similar idea, in this case, we used paint.net. We can put each image on a layer and then delete all white pixels on the top layer to emulate an XOR. We get this result:
Therefore, the flag is ahsCTF{br0_!t$_st@tiC}.